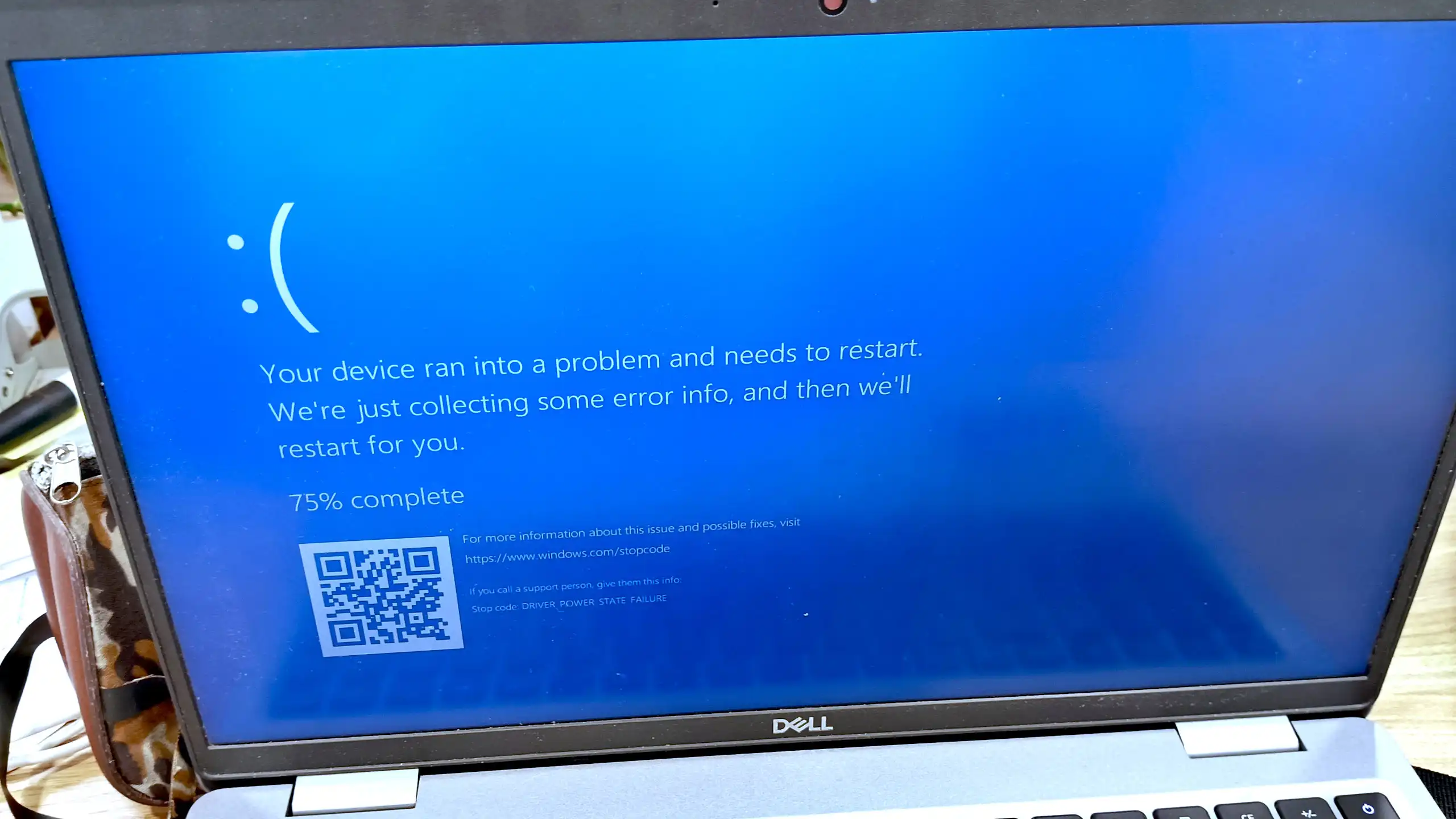
Yesterday, February 10th, was Patch Tuesday. Microsoft released security updates to address 58 new security vulnerabilities.
In addition to Windows and Office, Exchange Server, Internet Explorer, Azure, and the Windows Subsystem for Linux (WSL) are also affected. Six zero-day vulnerabilities are already being exploited in the wild, and five vulnerabilities are classified as critical.
The next Patch Tuesday is expected on March 10th, 2026.
Microsoft Windows updates
A large number of the fixed security vulnerabilities—31 this time—are spread across the various Windows versions (10, 11, Server) for which Microsoft still offers security updates. Windows 10 is still listed as an affected system, even though support officially expired in October.
Two Windows zero-day vulnerabilities were already publicly known and are being exploited in the wild. Both are SFB (Security Feature Bypass) vulnerabilities. The CVE-2026-21510 vulnerability in the Windows Shell allows an attacker to bypass SmartScreen and Shell security checks in order to execute arbitrary code. A user merely has to open a shortcut for the malicious code to be executed.
Anyone who thought they were finally rid of the old browser zombie Internet Explorer (IE) is mistaken. It’s still present in all versions of Windows, as many programs still rely on certain IE functions. These legacy issues are decreasing over time, but still exist. Attackers can exploit SFB vulnerability CVE-2026-21513 to bypass security checks and gain unauthorized access.
The CVE-2026-21519 vulnerability in Desktop Window Manager (DWM) is already the second DWM vulnerability this year to be exploited. Attackers can gain elevated privileges and execute code with system permissions. To do this, they combine the DMW vulnerability with an RCE vulnerability, of which there are plenty.
CVE-2026-21533 is another EoP (Elevation of Privilege) vulnerability. It’s found in the Remote Desktop Service. Contrary to what the affected Windows component might suggest, this bug is exploited locally to gain elevated privileges. As with the DWM vulnerability, if successful, an attacker can execute code with system privileges. Computers running the vulnerable Remote Desktop Service can be an interesting intermediate target for lateral movement after penetrating a network.
The last zero-day vulnerability in this series is CVE-2026-21525, a DoS vulnerability in the Remote Access Connection Manager. An attacker could crash the service. Since it’s unclear whether it will restart automatically, the attacker could potentially keep an administrator who wants to intervene remotely at bay. Otherwise, DoS vulnerabilities are rarely used in more complex attack scenarios.
Microsoft Office updates
Microsoft has fixed six vulnerabilities in its Office family, all of which are classified as high risk. At first glance, these don’t include any RCE (Remote Code Execution) vulnerabilities.
However, the Word vulnerability CVE-2026-21514, classified as a zero-day and SFB (Security Feature Bypass) vulnerability, can also be used to inject and execute code. At least the preview window is not an attack vector here—a user must open a prepared Office file using Word to enable a successful attack via this vulnerability.
Microsoft Azure updates
February’s Patch Tuesday doesn’t include any security vulnerabilities classified as critical when it comes to desktop computers or servers on local networks, but there are five security vulnerabilities identified as critical that affect Microsoft’s Azure cloud platform.
Microsoft has already fixed three of them and is in the process of documenting them. Two vulnerabilities affect confidential ACI containers (Azure Container Instances) and require action to secure them.
Microsoft Edge updates
The latest security update to Edge 144.0.3719.115 dates from February 5th and is based on Chromium 144.0.7559.133. It fixes two Chromium vulnerabilities. However, Google has since released Chrome and Chromium 145. A corresponding Edge update is expected to be released at the end of this week.
Microsoft has also closed a spoofing vulnerability (CVE-2026-0391) in Edge 143 for Android. This was already done back in December, but is only now being publicly documented.
This articles is written by : Nermeen Nabil Khear Abdelmalak
All rights reserved to : USAGOLDMIES . www.usagoldmines.com
You can Enjoy surfing our website categories and read more content in many fields you may like .
Why USAGoldMines ?
USAGoldMines is a comprehensive website offering the latest in financial, crypto, and technical news. With specialized sections for each category, it provides readers with up-to-date market insights, investment trends, and technological advancements, making it a valuable resource for investors and enthusiasts in the fast-paced financial world.