From smart but insecure door locks to Nvidia’s deepfake keynote, there are currently numerous forms of attack that are extremely dangerous.
The following 9 attacks stand out in particular and could also pose a threat in a similar form in 2026.
1. Malware in open source is on the rise
In 2024, the computer world narrowly escaped disaster: Over several years, attackers had been working to build a backdoor into the Linux operating system. A vulnerability in this system affects almost all users, as almost every internet server runs on Linux.
The attackers were on the verge of gaining undetected access to a large proportion of these servers. They had infiltrated the open source project XZ, which produces a compression tool, by posing as employees. They achieved this through social engineering and a great deal of patience.
The attack on the open-source software presumably began in 2021 and continued until early 2024. By that time, the backdoor had penetrated pre-release versions of Debian and other Linux systems. It was then only months away from being distributed to most internet servers worldwide.
The backdoor was not discovered by an antivirus specialist, but by Andres Freund, a Microsoft employee. Freund is a developer and works on the open-source database PostgreSQL on Linux.
He noticed that logging in via SSH (Secure Shell) took a little longer with the new pre-release version of Debian. Instead of the usual quarter of a second, the login took three-quarters of a second.
Other developers might not have noticed this difference or might have ignored it. However, Freund became suspicious and searched for the cause. Four days later, he had found the backdoor and warned the public.
Security researchers then assigned the XZ backdoor a CVSS (Common Vulnerability Scoring System) score of 10, the highest possible value.
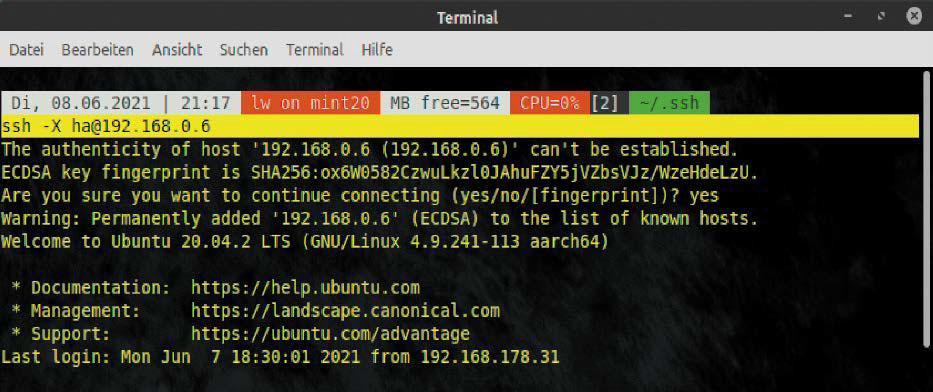
SSH is used to connect a PC to a Linux server. Keys are exchanged for security purposes. In 2024, a backdoor that could be exploited via SSH almost found its way into Linux servers.
Foundry
The attack on XZ is special for several reasons. On the one hand, there is the duration. The attacker took years to become a member of an open source project, gain the trust of the project manager, and integrate his code.
The malicious code and the entire attack chain are also noteworthy. It includes XZ Utils, Systemd, and SSH.
The same backdoor only opens for the attacker, who must send a secret key. All other SSH users are denied access to the backdoor. Finally, the discovery of the malicious code is also extraordinary — just in time and thanks to a single attentive developer.
It is alarming that this extraordinary attack on an open-source project is not an isolated case. Although the other attacks are less spectacular, they are all the more numerous.
This is possible because open-source software is based on openness: The code is accessible, customizable, and verifiable by anyone. Although there are security mechanisms in place, it is still relatively easy to provide infected packages, which are then used by developers.
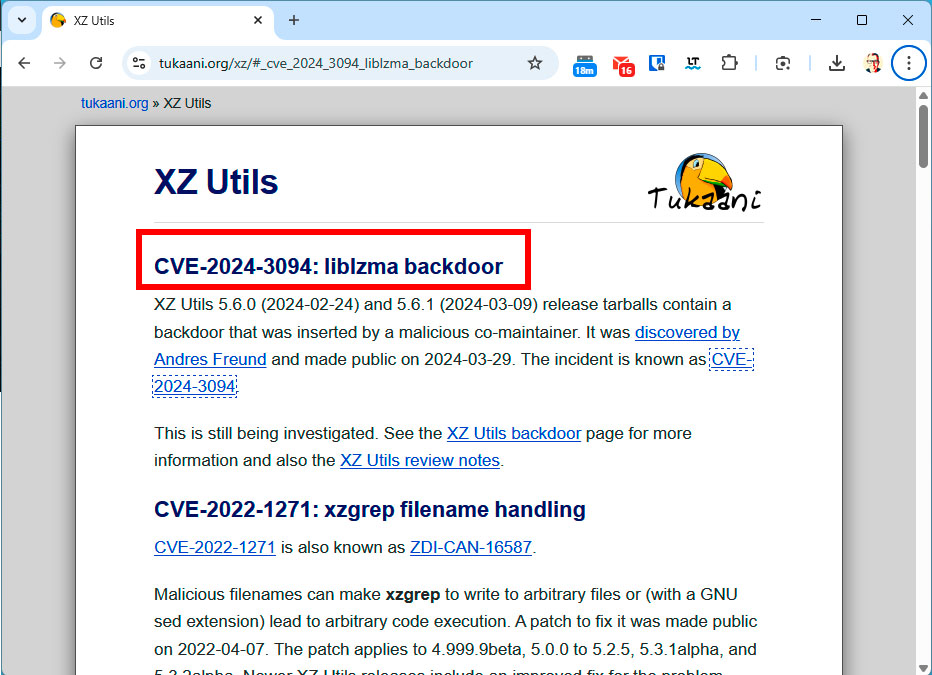
The security vulnerability in XZ Utils has been given a score of 10, which is the highest possible value. This shows that the vulnerability can be easily exploited and cause significant damage.
Foundry
Antivirus manufacturer Kaspersky also draws attention to this. According to an analysis, cybercriminals hid a total of 14,000 malicious packages in open-source projects in 2024. This represents an increase of 50 percent compared to the previous year.
The experts at the cybersecurity provider examined 42 million versions of open-source projects for vulnerabilities. We do not yet have any figures for 2025. However, we do not expect a significant decline.
Danger: The risk to end users is more indirect. Most attacks are aimed at stealing data from companies. Accordingly, it is mainly enterprise software that is affected. However, data theft from companies ultimately also affects customers.
Protection: For developers who integrate open source into their projects, as well as for companies that work with open source, security provider Kaspersky offers an information feed on problematic code.
The feed reports the following types of threats: packages with vulnerabilities, packages with malicious code, packages with riskware such as crypto miners, hacking tools, etc., compromised packages containing political slogans.
Access to the feed can be requested at kaspersky.com/open-source-feed.
Software companies can also access tools from security experts such as Xygeni Security. The company specializes in protecting the software supply chain. End users must rely on their installed virus protection. See our article on the best antivirus programs.
2. Unsubscribe button steals data
Every newsletter must contain an unsubscribe button that allows you to unsubscribe.
Danger: Not every unsubscribe link is harmless. One in 650 of these buttons does not lead to the desired unsubscribe page, but to a phishing website that wants to steal data or spread malware. This is reported by the security company DNS Filter.
Anyone who clicks on an unsubscribe link automatically confirms that their email address exists and that they check their inbox. For spammers, who usually extract their email addresses from large data packages, this information alone is valuable.
If the spammers go to the trouble of designing the supposed unsubscribe page in such a way that it extracts data from visitors, they use social engineering tricks to elicit passwords and other sensitive information from their victims.
Protection: Instead of clicking on the unsubscribe button, you can block the sender in your email program or in the web interface of your email provider. If this is not possible, you can add the email and thus the sender to a spam list.
This will prevent any further messages from this sender from reaching your inbox. You will then only need to remember to unblock the sender if you want to receive messages from them again.
However, this will never be the case with the phishing emails we are discussing here.
- In Outlook, right-click on an email and select “Block” → “Block sender”.
- In Thunderbird, select the email and click on “Junk” at the top.
- In Gmail, open the message and then select the three-dot menu at the top right of the email. In the menu, click on “Report spam” or “Block sender”.
3. Captcha introduces malware
Captchas are designed to protect websites from automated requests by distinguishing real people from bots. Nowadays, this often requires nothing more than clicking on the “I’m not a robot” checkbox.
In the past, you had to click on small photo squares showing cars, traffic lights, or motorcycles.
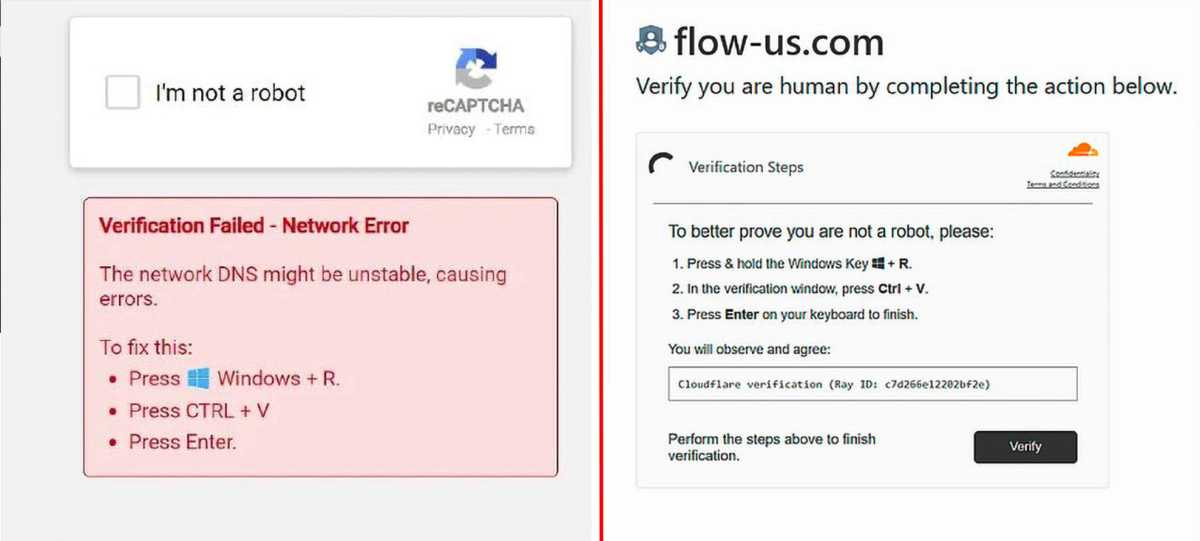
New trap with captchas: After clicking on the hostile captcha “I’m not a robot”, one of these instructions appears. If you follow it, you insert a previously copied malicious code into the Windows Run dialog, which then downloads the actual virus.
Foundry
Danger: For some time now, criminals have been using captchas to smuggle viruses such as the Qakbot malware onto the PCs of website visitors, as follows:
- When you first click on the “I’m not a robot” checkbox, the website copies malicious code to the page visitor’s clipboard.
- Instructions then appear, which the user is supposed to follow because a network error has allegedly occurred, or to continue verifying that they are a human and not a machine. The instructions specify the key combinations Win-R and Ctrl-V, followed by the Enter key.
- However, what this actually does is open the Windows Run dialogue box (Win-R), paste the malicious code from the clipboard into it (Ctrl-V), and execute it (Enter).
- The code then downloads the actual malware, usually Qakbot. This adds the PC to a botnet or downloads ransomware that encrypts all data and then demands a ransom.
Protection: The Run dialogue box should serve as a clear warning. No legitimate captcha in the world should want to paste code there. Remain suspicious and don’t be afraid to cancel an action.
4. Spyware Trojans in the App Store
A new type of spyware Trojan is stealing from users of Android and iOS smartphones. The malware, known as Spark Cat, was found in apps available in the official Google and Apple app stores. After installing the infected app, it requests access to the photo storage.
This does not usually arouse suspicion, as Spark Cat and its successor Spark Kitty hide in chat apps, for example.
Sending photos via chat apps is common and naturally requires access to photos.

This app was available in Google’s official app store and was infected with the Spark Cat spyware Trojan. The malware searches the smartphone’s image storage for passwords, which it extracts using OCR.
Foundry
Danger: On Google Playalone, Kaspersky’s security researchers counted 10 apps infected with Spark Kitty that had been downloaded over 240,000 times. In Apple’s App Store, the malware was found in 11 infected apps.
The malware searches the phone’s photo storage for screenshots containing passwords or other secret information. The text is extracted using OCR recognition and then used by the attackers to access crypto wallets. This allows them to steal large sums of money from their victims’ accounts.
Protection: The tried-and-tested method of only downloading apps from official app stores is unfortunately of no help here. After all, the malware was found in apps from these stores. In future, you should therefore also pay attention to how often an app has been downloaded. Apps with a million or more downloads are most likely safe.
Also, pay attention to the permissions an app requests. You should only grant access to your photo storage after careful consideration. And as a general rule, sensitive information such as passwords should not be stored in screenshots. These belong in a password manager. See our article on the best password managers.
5. Attacks on printers
In June 2025, security researchers at Rapid 7 discovered eight vulnerabilities in hundreds of printers from various manufacturers.
Danger: Attackers can use these vulnerabilities to gain access to the network and data. The companies affected are Brother, Fujifilm, Ricoh, Toshiba, and Konica Minolta. Although the companies have provided firmware updates, the security vulnerability can only be closed with a workaround.
This vulnerability bypasses authentication, allowing attackers to gain control of the device. To log in, attackers use the device’s default password, which consists of its serial number. This can be retrieved via another vulnerability.
Protection: Change your printer’s default password and install the latest updates for your device.
6. Browser add-ons empty crypto wallets
Browser extensions containing malicious code are popping up again and again. Most recently, the criminals behind these extensions targeted owners of crypto wallets.
This is a Firefox extension for the Meta Mask crypto exchange. It is often difficult to determine whether these extensions are harmless or not. However, a high number of downloads suggests that an add-on is harmless. Taking a look at the developer’s website also helps with the assessment.
Foundry
Danger: Dozens of fake browser add-ons for Firefox are designed to steal access data for cryptocurrency wallets. The extensions pretend to be legitimate wallet tools from well-known platforms such as Coinbase, Meta Mask, or Trust Wallet.
Some of the approximately 40 dangerous add-ons are even said to have made it into Firefox’s official add-on marketplace, as reported by the discoverer Koi. To do this, the attackers used the open-source code of well-known add-ons and placed their malicious code in them.
The add-on was then posted online under a name similar to the original.
Protection: Only download browser extensions from trusted sources. Even then, make sure that the add-on has been downloaded many times before.
Since extensions can update automatically, there is also a risk that add-ons that were initially harmless could be infected with malicious code after an update. Therefore, uninstall any extensions that you no longer need.
7. Deepfakes
Deepfakes are fake photos, audio files, or videos. They can cause a lot of damage, because even cautious people can be misled by the fakes.
One example is a fake livestream of Nvidia’s keynote speech in October 2025: At the same time as the real livestream on YouTube, fraudsters broadcast a deepfake video featuring an AI-generated Jensen Huang, CEO of Nvidia.
However, he did not talk about new chips at Nvidia, but about a new cryptocurrency project. The fake stream is said to have had more viewers than the real one at the beginning: 100,000 for the deepfake compared to 12,000 for Nvidia.
The reason for this was probably that YouTube displayed the deepfake first in the results list when searching for “Nvidia Keynote.” It took YouTube half an hour to take the fake offline.
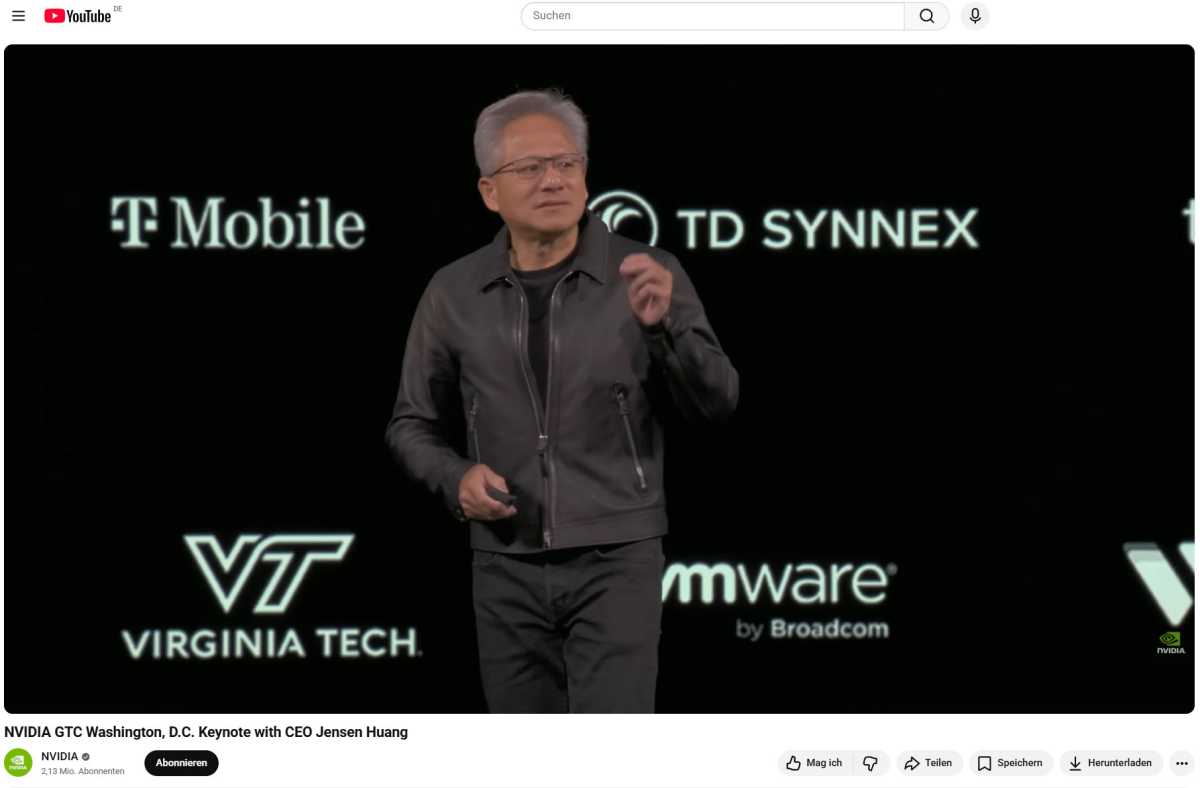
The real Jensen Huang, CEO of Nvidia, at the real keynote in October 2025. At the same time, a deepfake of the keynote with Jensen Huang was running on YouTube. In it, he advertised a cryptocurrency.
Foundry
Danger: Criminals use cryptocurrencies to steal money from unwary users. These scams usually involve false promises of quick profits with crypto coins that are actually worthless. Deepfakes are often used for this purpose.
Manipulation is then used to quickly increase the apparent value of the coins, which prompts the victims to buy. Once a certain value is reached, the fraudsters sell their shares in one fell swoop and make a profit. The price of the cryptocurrency falls rapidly, so that everyone else usually suffers a complete loss.
Protection: You should only invest in cryptocurrencies if you are very familiar with the subject. Then the typical crypto scams are easy to spot.
8. Ransomware with AI
Security researchers at Eset have discovered malware called Prompt Lock. It uses artificial intelligence specifically for ransomware attacks.
Danger: The blackmail virus uses a locally installed language model that independently generates scripts during the attack and thus decides for itself which files to search, copy, or encrypt.
A function for the permanent destruction of files is apparently already integrated, but has not yet been activated. Prompt Lock creates cross-platform Lua scripts that can run on Windows, Linux, and Mac OS.
Protection: The best protection against ransomware is an up-to-date data backup that is stored separately from the system. You can find more tips in our guide to ransomware.
9. Attackers crack doors
Smart devices for home networks usually also offer internet access to their functions. While this is convenient, it also carries risks.

The management software for Unifi’s smart door locks contained a security vulnerability with the highest vulnerability rating (CVSS 10). Hackers could probably easily crack a door protected by Unifi.
Unifi
Danger: Vulnerabilities in smart devices become threatening when an attacker can use them to penetrate the home network and steal data. The following case is also very unpleasant: A smart doorbell has a vulnerability that attackers can use to open the lock.
This was apparently the case in October 2025 with door locks from the company Unifi. The Unifi Access Application access software contained a security vulnerability with a CVSS score of 10, as announced by the manufacturer itself.
It did not reveal exactly what the vulnerability and the corresponding attack methods look like. However, the CVSS score of 10, which is the highest possible rating, suggests that the vulnerability can be easily exploited with massive consequences.
Protection: Version 3.4.31 of Unifi Access Application, which is aimed at businesses, is affected by the vulnerability. Administrators should update to the latest version.
In general, you should regularly check for updates to the firmware and management software for all smart home and network devices. Vulnerabilities in these devices can have serious consequences.
This articles is written by : Nermeen Nabil Khear Abdelmalak
All rights reserved to : USAGOLDMIES . www.usagoldmines.com
You can Enjoy surfing our website categories and read more content in many fields you may like .
Why USAGoldMines ?
USAGoldMines is a comprehensive website offering the latest in financial, crypto, and technical news. With specialized sections for each category, it provides readers with up-to-date market insights, investment trends, and technological advancements, making it a valuable resource for investors and enthusiasts in the fast-paced financial world.
