For months now, North Korea has been targeting crypto developers via NPM supply chain attacks. This is a highly sophisticated global campaign orchestrated by the infamous Lazarus group to steal funds and data through supply chain attacks.
Starting in August 2024, the group has been inserting malicious JavaScript into GitHub repositories and NPM packages. This operation is named Marstech Mayhem, and the malware’s assigned title is Marstech1, Computing reported.
What’s more, Marstech1 targets popular cryptocurrency wallets. Various reports have named MetaMask, Exodus, and Atomic.
The malicious code enters the system undetected, scans for the wallets across Windows, macOS, and Linux, seizes control of browser configuration files, and starts intercepting transactions and extracting metadata.
This approach increases the risk of the malicious code spreading, therefore raising the threat to the global software supply chain significantly. Others may unknowingly download the compromised software packages, introduce them into different applications, and expose countless other users to danger.
Global Operation from North Korea Targeting Crypto Devs
The group presumed to be Lazarus hides the malicious JavaScript implant in GitHub repositories and NPM packages – which are typically used by crypto devs and Web3 developers, according to a report by The Registar.
NPM is the default package manager for the Node.js platform. It is used to install, publish, and manage Node.js packages. In fact, according to Contrast Security, NPM “is the single largest language code repository globally.”
A report by cybersecurity company SecurityScorecard stated on 30 January that Lazarus has been altering legitimate software packages by embedding obscured backdoors and then tricking developers into executing these compromised packages.
“To the untrained eye it goes unnoticed by the victim and successfully executes. These packages may involve anything from cryptocurrency applications to authentication solutions,” the report said.
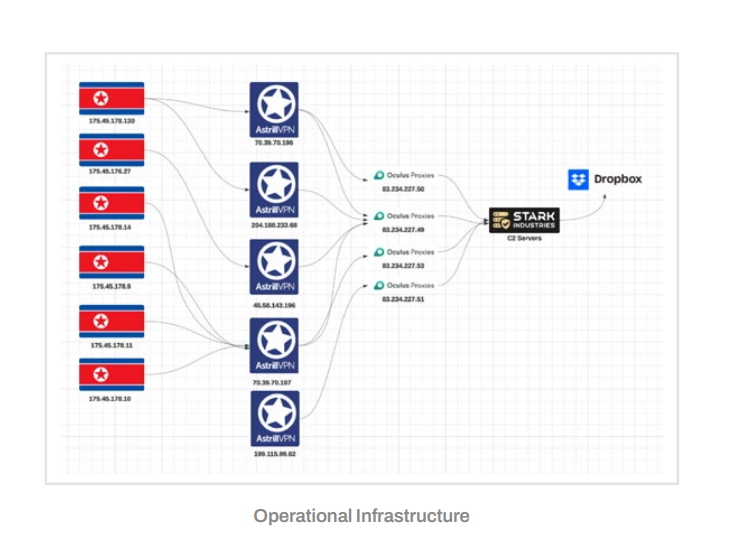
SecurityScorecard found 233 confirmed individual victims who have installed the new Marstech1 implant between September 2024 and January 2025. Many features of this code “demonstrate North Korea’s evolving tradecraft,” it said.
What’s more, the implant now comes with multiple obfuscation layers, showcasing a constant effort to advance the technique and stay ahead of detection measures.
Therefore, the crypto/Web3 devs’ dependence on NPM combined with Marstech1’s ability to conceal itself pose a massive danger to the space.
“This analysis makes it evident that Lazarus was orchestrating a global operation targeting the cryptocurrency industry and developers worldwide,” the report reads. “The campaigns resulted in hundreds of victims downloading and executing the payloads, while, in the background, the exfiltrated data was being siphoned back to Pyongyang.”
The post N.Korean Hackers Boost Crypto-Looting Methods: Hiding Malware in GitHub, NPM Packages appeared first on Cryptonews.
This articles is written by : Nermeen Nabil Khear Abdelmalak
All rights reserved to : USAGOLDMIES . www.usagoldmines.com
You can Enjoy surfing our website categories and read more content in many fields you may like .
Why USAGoldMines ?
USAGoldMines is a comprehensive website offering the latest in financial, crypto, and technical news. With specialized sections for each category, it provides readers with up-to-date market insights, investment trends, and technological advancements, making it a valuable resource for investors and enthusiasts in the fast-paced financial world.
