Reports find that a new crypto malware has targeted hundreds of web3 job seekers through a malicious “GrassCall” meeting app.
Per Bleeping Computer, Russian team of hackers known as “Crazy Evil,” carried out a social engineering campaign that lured job seekers with fake interviews. The attackers used a malicious meeting app “that installs information-stealing malware to steal cryptocurrency wallets.”
The attack was initially flagged by several impacted users on Telegram, helping affected users to navigate through the loss. The malware is designed to infect both Mac and Windows devices.
GrassCall’s Social Engineering Tactics
Choy Kwok, a web3 professional, posted on X early this week, warning followers about the scam. He cautioned users not to download any meeting app that was asked by recruiters pretending to be from Chain Seeker.
Crypto Jobs List, a web3 job portal, carried several job listings for a blockchain-based platform ‘ChainSeeker.io’. However, little did the applicants know that perpetrators were behind the job scam. The jobs were also listed on LinkedIn and X, from legitimate-looking fake profiles.
“Setting up time to speak with them will take you to GrassCall. Do not download anything,” Kwok wrote.
Aspirants who applied for jobs via the portal, were reportedly asked to reach out to the company’s Chief Marketing Officer via Telegram to coordinate the meeting.
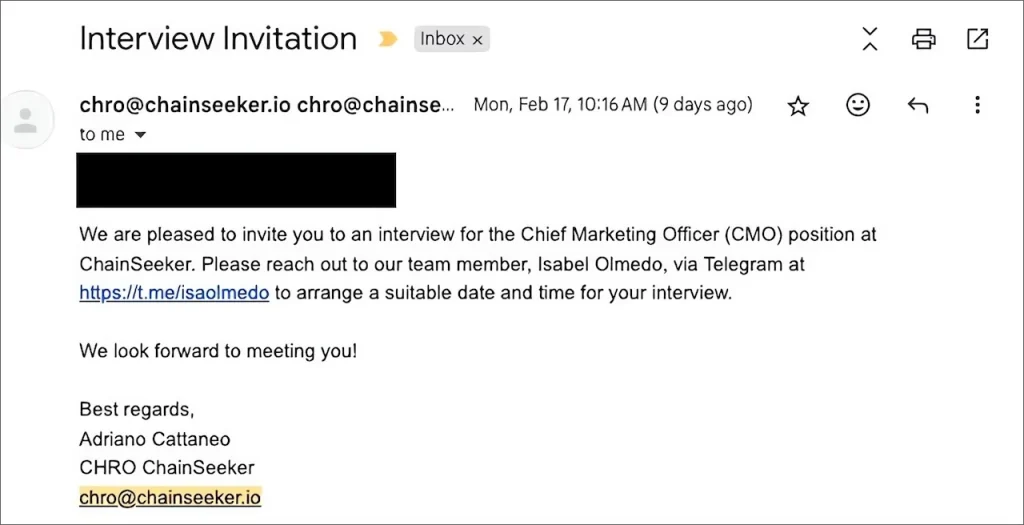
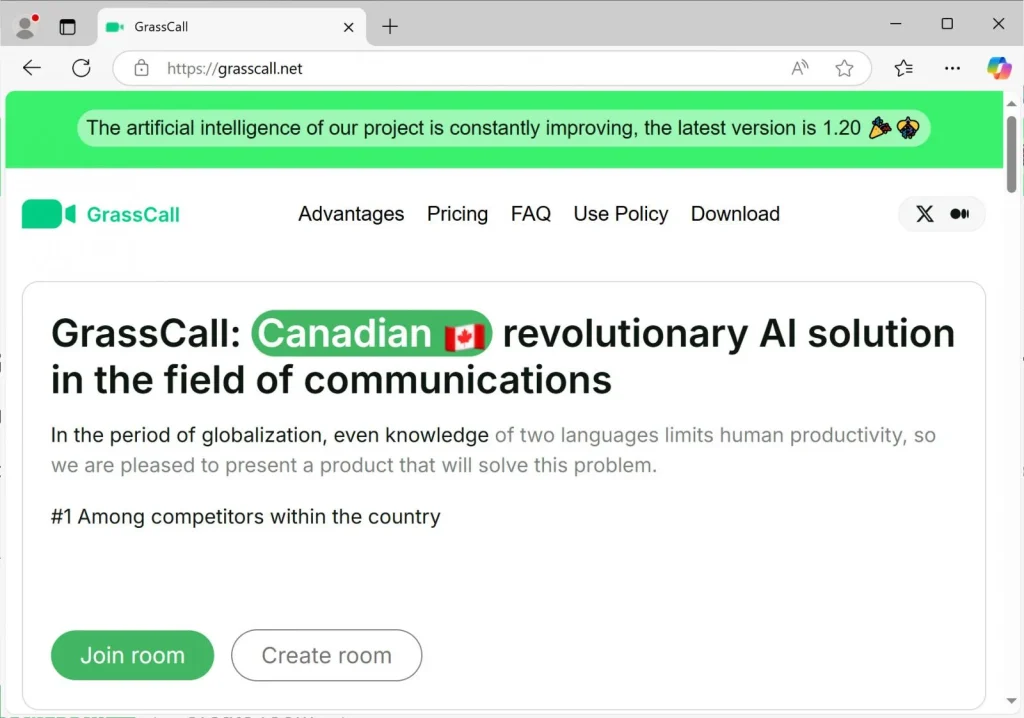
They were then asked to download a video meeting software GrassCall, with a website link and call code. The website “grasscall[.]net” led to a download link that described GrassCall as a “revolutionary AI solution in the field of communications.”
Atomic Stealer Malware Drains Cryptos From Victim Wallets
According to a cybersecurity researcher g0njxa, GrassCall website is a clone of a “Gatherum” website, which was used by the same Russian group in previous campaigns.
The GrassCall app prompts to enter a code shared by the fake CMO, and installs remote access trojans (RATs). The RAT then installs the Atomic (AMOS) Stealer malware on Macs.
“The rat is used to create persistence in the machine, add a keylogger for password too and deploying seed phishing for the hard wallets,” G0njxa told Bleeping Computer.
Once the malware takes control of the computer, it attempts to steal files based on keywords, cryptocurrency wallets, and passwords.
If a crypto wallet is found with the extracted password, the assets in the wallet are drained, he explained.
This comes parallelly with the recent widespread malware campaign targeting users on GitHub, flagged by cybersecurity firm Kaspersky.
The post Russian Hackers Use Malicious ‘GrassCall’ Meeting App to Drain Crypto Wallets: Report appeared first on Cryptonews.
This articles is written by : Nermeen Nabil Khear Abdelmalak
All rights reserved to : USAGOLDMIES . www.usagoldmines.com
You can Enjoy surfing our website categories and read more content in many fields you may like .
Why USAGoldMines ?
USAGoldMines is a comprehensive website offering the latest in financial, crypto, and technical news. With specialized sections for each category, it provides readers with up-to-date market insights, investment trends, and technological advancements, making it a valuable resource for investors and enthusiasts in the fast-paced financial world.
