The mad lads at watchTowr are back with their unique blend of zany humor and impressive security research. And this time, it’s the curious case of backdoors within popular backdoors, and the list of unclaimed domains that malicious software would just love to contact.
OK, that needs some explanation. We’re mainly talking about web shells here. Those are the bits of code that get uploaded to a web server, that provide remote access to the computer. The typical example is a web application that allows unrestricted uploads. If an attacker can upload a PHP file to a folder where .php files are used to serve web pages, accessing that endpoint runs the arbitrary PHP code. Upload a web shell, and accessing that endpoint gives a command line interface into the machine.
The quirk here is that most attackers don’t write their own tools. And often times those tools have special, undocumented features, like loading a zero-size image from a .ru domain. The webshell developer couldn’t be bothered to actually do the legwork of breaking into servers, so instead added this little dial-home feature, to report on where to find all those newly backdoored machines. Yes, many of the popular backdoors are themselves backdoored.
This brings us to what watchTowr researchers discovered — many of those backdoor domains were either never registered, or the registration has been allowed to expire. So they did what any team of researchers would do: Buy up all the available backdoor domains, set up a logging server, and just see what happens. And what happened was thousands of compromised machines checking in at these old domains. Among the 4000+ unique systems, there were a total of 4 .gov. domains from governments in Bangladesh, Nigeria, and China. It’s an interesting romp through old backdoors, and a good look at the state of still-compromised machines.
The Cameras are Leaking
One of the fun things to do on the Internet is to pull up some of the online video feeds around the world. Want to see what Times Square looks like right now? There’s a website for that. Curious how much snow is in on the ground in Hokkaido? Easy to check. But it turns out that there are quite a few cameras on the Internet that probably shouldn’t be. In this case, the focus is on about 150 license plate readers around the United States that expose both the live video stream and the database of captured vehicle data to anyone on the Internet that knows where and how to look.
This discovery was spurred by [Matt Brown] purchasing one of these devices, finding how easy they were to access, and then checking a service like Shodan for matching 404 pages. This specific device was obviously intended to be located on a private network, protected by a firewall or VPN, and not exposed to the open Internet. This isn’t the first time we’ve covered this sort of situation, and suggests an extension to Murhpy’s Law. Maybe I’ll refer to it as Bennett’s law: If a device can be put on the public Internet, someone somewhere inevitably will do so.
Some related research is available from RedHunt Labs, who did a recent Internet scan on port 80, and the results are a bit scary. 42,000,000 IP addresses, 1% of the IPv4 Internet, is listening on port 80. There are 2.1 million unique favicons, and 87% of those IPs actually resolve with HTTP connections and don’t automatically redirect to an HTTPS port. The single most common favicon is from a Hikvision IP Camera, with 674,901 IPs exposed.
The Big Extension Compromise
One of the relatively new ways to deploy malicious code is to compromise a browser plugin. Users of the Cyberhaven browser plugin received a really nasty Christmas present, as a malicious update was pushed this Christmas. The Cyberhaven extension is intended to detect data and block ex-filtration attempts in the browser, and as such it has very wide permissions to read page content. The malicious addition looked for API keys in the browser session, and uploaded cookies for sites visited to the attacker. Interestingly the attack seemed to be targeted specifically at OpenAI credentials and tokens.
This started with an OAuth phishing attack, where an email claimed the extension was in danger of removal, just log in with your Chrome Developer account for details. The Cyberhaven clicked through the email, and accidentally gave attackers permission to push updates to the extension. This isn’t the only extension that was targetted, and there are other reports of similar phishing emails. This appears to be a broader attack, with the first observed instance being in May of 2024, and some of the affected extensions used similar techniques. So far just over 30 compromised extensions have been discovered to be compromised in this way.
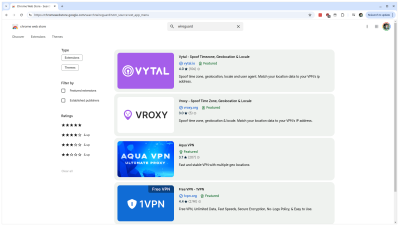
And while we’re on the topic of browser extensions, [Wladimir Palant] discovered the i18n trick that sketchy browser extensions use to show up in searches like this one for Wireguard.
The trick here is internationalization, or i18n. Every extension has the option to translate its name and description into 50+ languages, and when anyone searches the extension store, the search term can match on any of those languages. So unscrupulous extension developers fill the less common languages with search terms like “wireguard”. Google has indicated to Ars Technica that it is aware of this problem, and plans to take action.
Safety Labels
The US has announced the U.S. Cyber Trust mark, a safety label that indicates that “connected devices are cybersecure”. Part of the label is a QR code, that can be scanned to find information about the support timeline of the product, as well as information on automatic updates. There are some elements of this program that is an obviously good idea, like doing away with well known default passwords. Time will tell if the Cyber Trust mark actually makes headway in making more secure devices, or if it will be just another bit of visual clutter on our device boxes? Time will tell.
Bits and Bytes
SecureLayer7 has published a great little tutorial on using metasploit to automatically deploy known exploits against discovered vulnerabilities. If Metasploit isn’t in your bag of tricks yet, maybe it’s time to grab a copy of Kali Linux and try it out.
Amazon, apparently, never learns, as Giraffe Security scores a hat trick. The vulnerability is Python pip’s “extra-index-url” option preferring to pull packages from PyPi rather than the specified URL. It’s the footgun that Amazon just can’t seem to avoid baking right into its documentation. Giraffe has found this issue twice before in Amazon’s documentation and package management, and in 2024 found it the third time for the hat trick.
It seems that there’s yet another way to fingerprint web browsers, in the form of dynamic CSS features. This is particularly interesting in the context of the TOR browser, that turns off JavaScript support in an effort to be fully anonymous.
And finally, there seems to be a serious new SonicWall vulnerability that has just been fixed. It’s an authentication bypass in the SSLVPN interface, and SonicWall sent out an email indicating that this issue is considered likely to be exploited in the wild.
This articles is written by : Nermeen Nabil Khear Abdelmalak
All rights reserved to : USAGOLDMIES . www.usagoldmines.com
You can Enjoy surfing our website categories and read more content in many fields you may like .
Why USAGoldMines ?
USAGoldMines is a comprehensive website offering the latest in financial, crypto, and technical news. With specialized sections for each category, it provides readers with up-to-date market insights, investment trends, and technological advancements, making it a valuable resource for investors and enthusiasts in the fast-paced financial world.